
For electronic payments, Point-of-Sale (POS) systems are a complex digital process, making retailers and customers vulnerable to cyberattacks.
From the moment you swipe or tap your card at a Point-of-Sale (POS) terminal, you are part of a complex digital ecosystem that is vulnerable to cyber threats. Beyond processing transactions, POS systems are multifunctional — they manage inventory, synchronize with customer relationship management (CRM) software, and connect to overall retail management systems. However, as they handle vast amounts of data, including personal and financial customer information, these terminals are prone to network and data vulnerabilities. According to Statista, malware attacks, which include POS systems, are a significant cause for concern, reaching 5.5 billion in 2022.
Understanding Cybersecurity Risks in Retail Applications
Cybercriminals operate as “digital pickpockets,” employing sophisticated tactics to access and steal valuable data from POS terminals. As such, a successful breach could mean thousands of compromised credit details, potentially causing financial chaos for customers and businesses.
But how exactly do breaches occur? Whenever individuals use their card at a POS terminal for transaction approval, the information on the card’s magnetic stripe, such as the card number, the holder’s name, and the expiry date of the card, is transmitted with the transaction request to the payment application and then to the firm’s payment processor. Although this data is secured via encryption when it leaves the POS system and the firm’s network, for a brief time, it resides unencrypted in the system’s RAM. During this phase, the data is prone to being accessed by any malicious software that might be present on the device.
POS systems have been compromised in network breaches where unsecured or weak network infrastructure provides easy access for cybercriminals to steal sensitive data such as customer credit card numbers. For example, in 2019, POS malware was discovered in over 800 of Wawa’s convenience stores. The attack went undetected for 8 months and resulted in compromised payment information, including the names of customers, their card numbers and expiration dates.
Another nightmare to retailers is the older, but still prevalent “ram scraping” technique: bad actors attempt to steal customers’ credit card details before it is encrypted by a POS system. Variants like screen capture tools and keystroke monitoring software also exist. As their names suggest, these are malicious programs engineered to stealthily record personal data either when it’s shown on a screen or during entry, and relay this information to an external entity.
Balancing Edge Security, Efficiency, and Adaptability
Protecting retail systems from cyber threats is all about securing the edge—the frontend of retail transactions—from network and data security breaches. This protection involves implementing multi-layered security, including firewalls and anti-malware solutions, while ensuring compliance with industry standards, like PCI DSS. Albeit, security solutions must not come at the cost of performance or adaptability: they need to be agile, efficient, and ready to face evolving threats.
Ensuring Robust Protection with Alif Ensemble MCUs

Alif Semiconductor Ensemble MCUs prevent data interception and tampering during Point-of-Sale data exchanges.
In smart retail applications, Alif Semiconductor Ensemble MCUs provide robust protection to ensure the confidentiality and integrity of transactional data. By implementing TLS protocols and PKI certificates, they provide strong encryption for data exchange between POS systems and financial networks. These measures are critical in preventing data interception, tampering, and fraudulent operations. These MCUs also contribute to inventory management by encrypting and securing critical information like pricing and stock levels, while preventing unauthorized access.
Alif Semiconductor’s approach to edge security is not just about addressing current threats, but also adapting to future challenges. Their Ensemble MCUs are designed with a multi-stage lifecycle management encompassing product manufacturing, product provisioning, deployment, and end-of-life. Alif Semiconductor ensures that every stage of the product life is securely managed.
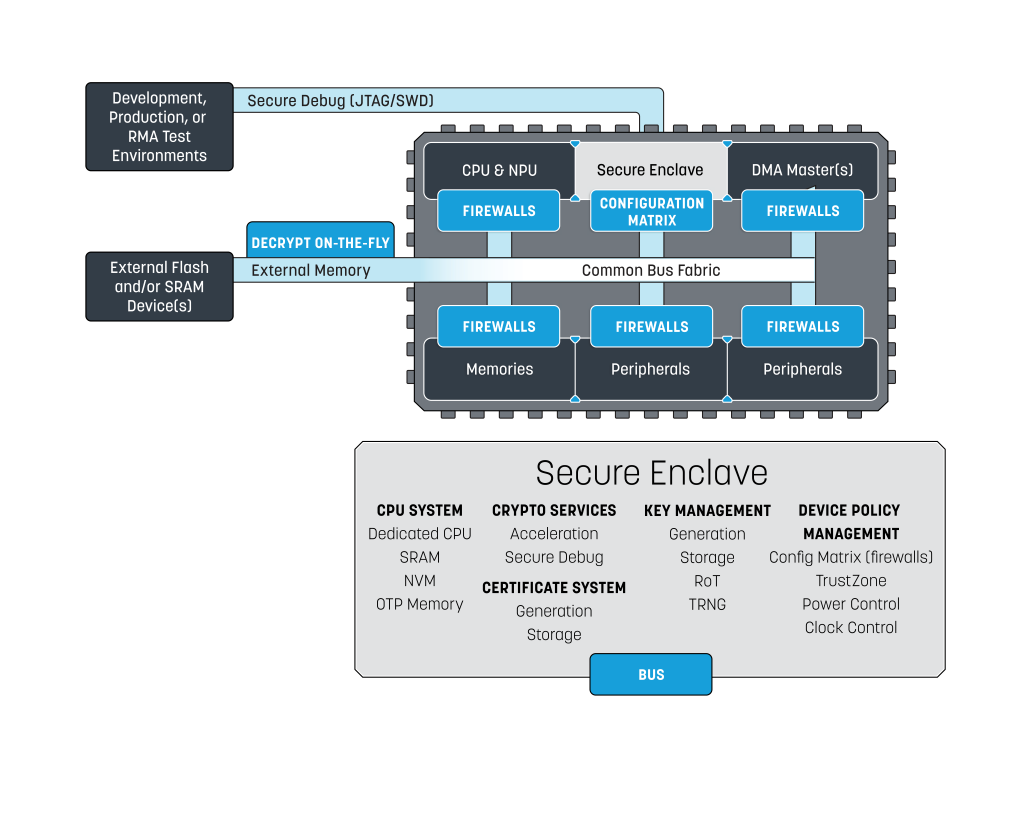
At the heart of Ensemble MCUs is an independent, isolated security subsystem — a “Secure Enclave” that protects various assets within the chip including CPU cores, interfaces, memory and data, as well as code and IP algorithms. This security subsystem has a dedicated CPU, memory, cryptographic hardware, OTP memory, and holds the hardware-based Root of Trust for the device. To further enhance security, Alif Semiconductor provides a unique device ID and key pair for each individual chip to secure all potential points of failure. Please reference the Alif Semiconductor Security Whitepaper for a deep dive into available security offerings.